Home
The way we work is changing
Users want to access data from anywhere
Users want access to their data 24 x 7
More internal services are outsourced to the cloud
Digital supply chains are more distributed
More business data than ever is sent beyond your secure network perimeter.
Exposing your valuable outbound data to an ever greater risk of compromise.
Outbound data compromise
DATA THEFT from hackers or insider attacks
DATA THEFT from ransomware or botnets
POISONED application updates
REDIRECTED cloud services data

Antivirus protects against inbound data threats
Let ZORB protect against outbound data threats
Simple setup - no technical knowledge required
Hands off - no resource needed to continually maintain rulesets
Automated blocking - no IT intervention
Proactive blocking - eliminates alert fatigue
EASY
POWERFUL
Zero-trust - untrusted data does not leave the device
Prevent - STOP threats, not simply mitigating the risk
Compliance - easily achieve Cyber Essentials, ISO27001, regulation
Reputation protection - keep data breaches away from your brand
Low entry cost - affordable for any business, regardless of size
Ubiquitous - engineered to scale affordably across all devices
Avoid change - no need to update or replace legacy equipment
Manage your budgets - minimal upkeep impact on your IT staff
AFFORDABLE
From send & hope, to send & know
Start from a DENY ALL stance
Only data flows that pass all THREE crucial checks are transmitted
TRUSTED APPLICATION
Has data come from a trusted program?
TRUSTED DESTINATION
Is data going to a trusted recipient?
TRUSTED TRANSMISSION
Inline with company policy? e.g. VPN
If it's not trusted, it's not sent
Use Cases - Misconfig and Vulnerability
Misconfiguration and Vulnerabilities
Prevent data breaches from misconfiguration or vulnerabilities of apps and devices
The exploitation of a vulnerability or misconfiguration is the root cause of most data breaches. Most breaches start when a bad actor discovers an opening to the corporate network via a misconfigured device, unpatched software, or default device settings. Around 35% of data breaches can be attributed to a device or application misconfiguration.
Human error, lack of knowledge, unchanged default settings, or enabling unnecessary features can open a range of doors for an attacker. An estimated 84% of businesses have a high-risk vulnerability on their network perimeter. In 2019, lethargy in patching known vulnerabilities contributed to 60% of data breaches.
Despite regular patching, a determined attacker can force vulnerable code upon a business. MoveIT, Fujitsu, Microsoft are recent high-profile breaches that started with a third parties sending malicious applications updates containing compromised code. Most application updates start with a pull request from the device, with the application querying a central server for updates. Therefore, application update requests are an outbound data flow, that can be redirected.
The much-publicised SolarWinds hack in 2020 was a nation state sponsored attack, where the hackers compromised a third party’s system to deliver malicious code via a supposed vendor update. The code included a backdoor granting the attackers access to the SolarWinds Orion Platform. By encoding the malicious code within an update, the code was able to bypass antivirus and firewall protection.
Prevention
Due to the sheer volume of devices, hardware and applications on today’s corporate network, it might not be possible to 100% eliminate risk from vulnerabilities or misconfiguration.
Applying a zero-trust framework to outbound data can eliminate the risk of applications requesting updates from malicious endpoints.
ZORB queries the destination address of all outbound data flows. If the destination address is not tied to the application’s vendor IP address range, the data flow is blocked.
Use Case Example - Preventing malicious updates

A company recently upgraded to Windows 11. However, an old Win 95 PC could not be updated as it runs a core manufacturing sensor. An attacker found a vulnerability on this outdated device and was able to use this to introduce a malware to redirect all Microsoft update requests to a malicious server in China. This malicious update included a backdoor into Microsoft’s OS.
The company’s safelist has sxdhelper.exe, waasmedicagent.exe, sihclient.exe and other core windows applications as trusted. Additionally these are set as permitted to only communicate with Microsoft. The malware was able to associate itself with the trusted sxdhelper.exe application. However, ZORB noticed that the data transfer was not to a recognised Microsoft IP and blocked the update request.
The company then decided to roll out an AI-based note taking desktop application to all members of its management team. The vendor of the application “ainotes.exe” is www.wedonotes.com
An IT admin logged into their ZORB portal to amend the safelist. They added the application “ainotes.exe” with a trusted vendor destination of “WeDoNotes”. They also added “ainotesupdater.exe” with a trusted destination of “WeDoNotes”. The amended safelist was automatically updated on all the management team’s devices without the user, or IT having to do anything. Data flow, and update requests for this application are now only permitted to be sent to the vendor, and blocked if they are being sent anywhere else.
Summary
Misconfigurations and vulnerabilities are involved in most data breaches. Even with the best patching program, malicious code or DNS poisoning can force an application to update from an unreliable source. ZORB can block data transfer to IP addresses that are not associated with the vendor software application.
Start your outbound security journey
TODAY
Add outbound data to your security posture.
Use Cases - Cloud Data
Cloud Application Data Threats
Prevent data breaches from redirected outbound cloud services data
Most business are undergoing a shift in working patterns, as more services are outsourced to the cloud. This could simply be cloud-based data storage. Or it could be self-hosted cloud services on AWS. Or third-party services such as CRMs, ERP, project management, HR, finance, service desk ticketing, etc.
Today, over 60% of enterprise data is held in the cloud. This translates as over 90% of businesses with more than 11 employees using at least one cloud-based service.
Data breaches remain the biggest security concern for cloud-based services. These can arise for various reasons:
- vulnerabilities in cloud applications or infrastructures,
- compromised account credentials
- insider threats
- lack of encryption of data at rest or in transit.
With almost 45% of data stored in cloud services unencrypted, it can come with little surprise that in 2023, over 80% of data breaches involved data used in cloud services.
There is an inherent degree of trust when using cloud services, that the data transferred to the application goes directly to the cloud vendor and it not intercepted on route. An estimated 10% of data transfer (application data and backups) remains unencrypted. The amount of data intercept or redirected by a bad actor (say via DNS rerouting) is not known but is still a breach.
Consider the magnitude of a business’s activities that a hacker has visibility of by redirecting an Office 365 .OST file synchronisation.
Prevention
Often one is reliant upon the cloud service provider themselves to provide appropriate security measures.
The result is very little control over what security measures you can influence. At best this can be limited to account access control measures, such as strong passwords, multi-factor authentication and priviledge restrictions. Zero-trust frameworks in cloud infrastructure lags significantly behind zero-trust uptake in corporate network.
One area that zero-trust can be successfully applied by the service user is data transfer. Classifying data to ensure the appropriate level of protection transfer, together with proactive, context-aware outbound firewalling on the network perimeter.
ZORB takes a much simpler approach to achieve a zero-trust framework for outgoing cloud application data transfer. ZORB challenges the destination of any outbound data flow to ensure it is being sent to the appropriate IP addresses. If not, the outgoing data flow is blocked.
Use Case Example - Preventing cloud data theft

A primarily office-based HR employee uses a cloud-based ERP package from Acme.com. This has a local desktop application, called hr.exe, which synchronises in real-time with the cloud data. Malware on the user’s PC tries to mirror the ERP data transfer to a service hosted in Azure.
The company list hr.exe as a trusted application in the company’s safelist. The cloud application is also associated in the safelist with the vendors domain (www.acme.com). ZORB will identify two data streams. 1) The legitimate data transfer from hr.exe to the cloud provider (acme.com), which it permits as per the safelist. 2) The data transfer from hr.exe to a non-acme.com IP address, which is blocked as untrusted as this IP is not permitted in the safelist. If necessary, this data flow could additionally be queried, and blocked, at a protocol level.
The user goes home for the evening to complete the work on their home PC. The company allows BYOD, but enforces a VPN tunnel to the main office, from where all outbound data is sent. The user only has 5 minutes to work complete, so avoids the hassle of logging into the corporate VPN.
Whilst the hr.exe application is trusted on the user’s home device, ZORB has been set up to ONLY permit data transfer over the VPN. The destination IP is NOT the VPN endpoint, so the data is blocked. Having been blocked, the user realises the error and connects to the VPN. ZORB now transmits the data.
On Monday, the IT department rolls out a new cloud-based CRM package to all of sales team.
The IT admin logged onto their ZORB cloud portal, removed the old SalesSpot.exe entry from the trusted list and replaced it with HubForce.exe and the name of the application vendor. This update to the safelist was automatically rolled out to each users device without IT having to do anything.
Summary
As the uptake in cloud-based services skyrockets, knowing that application data transfer is secure is paramount. ZORB ensures cloud application data is going ONLY to the cloud service provider. ZORB can also enforce company policy such as VPN usage and prevent data leaks from applications attempting to bypass VPN.
Start your outbound security journey
TODAY
Add outbound data to your security posture.
Use Cases - C&C Malware
C&C Malware
Prevent data breaches from C&C malware – botnets, ransomware, RATs
There are many types of malware that, once installed, communicate with a Command & Control (C&C) server. This C&C server, typically hosted in the cloud, provides attackers with a way to centrally control and update malware. This makes these types of threats highly versatile and persistent.
This chatter between malware and controller includes things like keep-alive traffic to tell the C&C server that the malware is still live and running. Or it could be to the malware transferring screenshots, or keylogger captures of passwords etc.
Examples of C&C malware include botnets, ransomware or RATs (Remote Access Trojans). More than half of all malware victims are SMBs.
Some ransomware will contact their C&C server after installation, in order to obtain their encryption key. If this communication can be intercepted, it is often possible to prevent the ransomware from encrypting a device. In 2023, a business fell victim to a ransomware attack every 14 seconds.
RATs are a type of malware that gives attackers remote control of an infected system via a backdoor. RATs are usually delivered by email or malicious links. RATs such as NanoCore (healthcare, manufacturing, financial services) and Poison Ivy (defence, government, healthcare, financial services) have been used in targeted attacks and cyber espionage campaigns.
The use of cryptojacking malware to covertly mine cryptocurrency on infected systems has surged. Many variants use C&C servers to receive instructions and updates from attackers. Almost every part of the world experienced triple- or quadruple-digit jumps in cryptojacking incidents in 2023.
Advanced Persistent Threats (APTs), sophisticated threat groups often backed by nation-states, frequently use C&C infrastructure to maintain access to compromised networks for extended periods of time for cyber espionage or other malicious purposes.
Prevention
Defending against C&C malware is still a significant challenge for cybersecurity professionals. One reason is that as much as 50% of these malware are zero-day, which means an applicable antivirus signature has yet to be released.
Blocking the communication between the malware and C&C is key to stopping the threat. Even if malware installs, blocking outbound comms 1) prevents the malware from registering with its C&C and 2) prevents exfiltration of stolen data.
Some solutions, such as Cisco Umbrella, rely on DNS filtering to block malware comms at the DNS level.
ZORB takes a much simpler approach. Any communication from “untrusted” applications are blocked before the data flow can be established.
NOTE: ZORB are specialists in blocking outbound traffic. ZORB software is NOT a replacement for your device’s regular antivirus. ZORB does not monitor incoming data, so won’t detect malware being downloaded. Nor do we stop it from installing. We can, however, stop malware from sending data back to its C&C if it does install.
Use Case Example - Preventing ransomware

A user clicked an email link that downloaded ransomware onto their device. The ransomware was able to bypass the device antivirus and installed on their machine as a file called ransomware.exe.
The company’s safelist contains all trusted business applications. ZORB applies a “BLOCK” to all outgoing traffic, unless it has come from a safelisted application. “Ransomware.exe” is NOT in the safelist, so ZORB blocks all outbound communications from “ransomware.exe” to its C&C server.
The ransomware has been programmed to evade endpoint protection. It realises that its traffic is blocked. So it renames itself to “Word.exe” (a safelisted application)
The ransomware comms data is now originating from a so-called “trusted” application (fake Word.exe). Tools such as Microsoft Defender for Endpoint will allow this “trusted” traffic to be transmitted. ZORB can take security a level deeper by associating trusted destinations to trusted applications. In the company’s safelist, Word is permitted to talk only with the internal server or Microsoft’s cloud. ZORB sees that the “trusted” application’s data is bound to a server hosted in Russia. This is not a trusted destination, so the outbound data is blocked.
Finally, the ransomware tries to communicate with a compromised Microsoft IP via SSH.
ZORB sees that traffic is coming from a trusted application (fake Word.exe) and wants to go to a trusted IP address associated with the source application (fake Microsoft IP address). However, ZORB blocks covert channels, such as SSH, FTP, TOR, RDP, etc, unless specifically permitted in the safelist. Again, the ransomware’s attempt at outbound communication with its C&C is blocked.
Summary
Mitigating C&C malware such as botnets, RATs, ransomware involves a combination of multiple tools and controls. However, should a C&C malware evade endpoint protection, ZORB will automatically block outbound communication with a C&C server, without user or IT intervention.
Start your outbound security journey
TODAY
Add outbound data to your security posture.
Use Cases - Hackers & Insiders
Hackers & Insider Attacks
Prevent data breaches from hackers, insiders & disgruntled employees
The likelihood of data theft from external hackers and internal bad actors has increased. Bad actors can easily acquire sophisticated attack tools, many of which are starting to incorporate AI to automate finding weak spots within an organisation. Fuelled by the ease of selling data on the dark web, or holding businesses to ransom.
Attacks are increasingly becoming state-sponsored. Large hacking teams with access to state provided budgets are attacking businesses of all types and sizes for data and IP theft, or simply to cause disruption.
An insider attack is malicious activities initiated by trusted individual within an organisation. This might be a disgruntled employee, an opportunist contractor, or even lack of policy outlining a third-party’s responsibilities.
The risk posed by insider threats is growing at an even faster rate than from hackers. So much so, that the threat of insider attacks now features in many CISO’s top 5 concerns. Recent data indicates that more than half of organisations have encountered an insider threat within the past year, with 8% experiencing more than 20 incidents. 74% of organisations are believed to be vulnerable to insider attacks.
Both external and internal actors are often motivated by financial gain. These bad actors aim to exfiltrate sensitive business data to either resell on the dark web or to hold the business to ransom. Insider threats can originate from various sources, such as employees, vendors, contractors, or partners who have access to internal systems and data. Often, it is a trusted person with legitimate access to sensitive information during their normal course of work that perpetrates an attack. Some of the most common scenarios involves departing employees or contractors who steal confidential data, intellectual property, or trade secrets before leaving the organisation.
Prevention
It may not be possible to totally eliminate the likelihood of attack from a determined adversary. The correct strategy is to mitigate the opportunity for attack. An attacker only requires one vulnerability in the infrastructure, whilst a defender needs to plug every gap.
Effective mitigation of the risks form external hacker attacks and insider threats requires a comprehensive set of measures, including access control, data encryption, employee cyber awareness education, and more.
Despite best efforts in mitigating the likelihood of incoming attacks, at some point, a bad actor with access to the system will attempt to exfiltrate information. Now, the strategy can shift from mitigate to prevent.
Again, the attacker has the upper hand due to the multiple ways in which data can be extracted. Physical data extraction could involve a USB drive, or printed material. Digital extraction means transferring data over the internet to cloud storage.
ZORB specialises in preventing unauthorised digital exfiltration. By applying a zero-trust framework to outbound data, ZORB blocks the manual or software-based extraction of data to unknown or untrusted destinations.
Use Case Example - Preventing unauthorised data transfers

Before resigning to establish a competing business, an employee tries to save confidential Word documents to external cloud storage.
The company’s safelist identifies “Word” as a trusted application. However, the safelist is also configured to only permit data transfer from Word to either the company’s internal server or to Microsoft’s managed services.
Upon realizing they cannot save documents externally due to these restrictions, the employee installs Dropbox on their laptop.
IT have not locked down the laptop so Dropbox installs successfully. However, Dropbox is not included in the company’s safelist of trusted applications. Consequently, any attempt to transfer data using Dropbox is automatically thwarted.
Finally, the employee attempts to establish a SSH connection to a personal AWS instance.
ZORB prevents data transfers via covert channels such as SSH, TOR, FTP, SFTP, and others unless explicitly permitted in the company’s safelist. Hence, the employee was unable to make an SSH connection with the external server.
Summary
Mitigating the dangers from hacker or insider attacks involves a combination of multiple tools and controls. However, should a bad actor gain unauthorised access to sensitive data, ZORB will prevent digital exfiltration. ZORB can also enforce company policy such as what is permitted, and non-permitted, cloud storage or approved cloud applications.
Start your outbound security journey
TODAY
Add outbound data to your security posture.
ZORB Trial
Get Started Now!
Rollout protection to 10 devices for FREE
and bring outbound data into your cyber defence posture today.
No credit card needed
* We will send your FREE licenses & software download link to this email
What do I get?
10 x ZORB software licenses
1 x admin login for ZORB's Online Portal
(To view & manage your security posture)
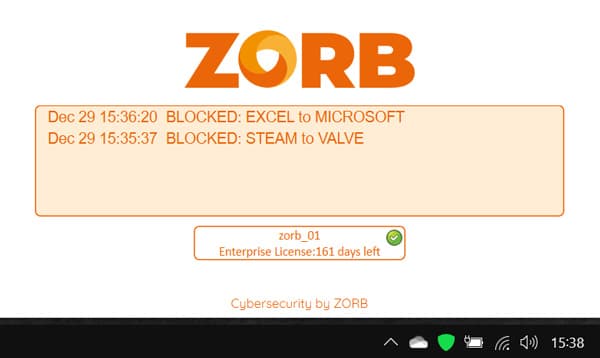
Block untrusted traffic to prevent:
– data theft due to hackers or insider attacks
– data theft from C&C malware (bots, ransomware, RATs)
– malicious redirection of cloud services data
– malicious application updates
→ Any questions, contact us at info@zorbsecurity.com
I'm ready to buy more licenses
Ready to eliminate data theft from your entire device estate?
Sandbox
Try a live sandbox of ZORB
Explore our sandboxed Administrator’s Portal to see data risk insights you can gain.
See ZORB in action using real-time live data from one of our employees’ devices running ZORB software.
(Without talking to a sales person)
What will I see in the sandbox?
You will be connected to a real online Admin Portal, that is used to manage a data risk posture.
Understand the insights an administrator in your business will have access to when using our service.
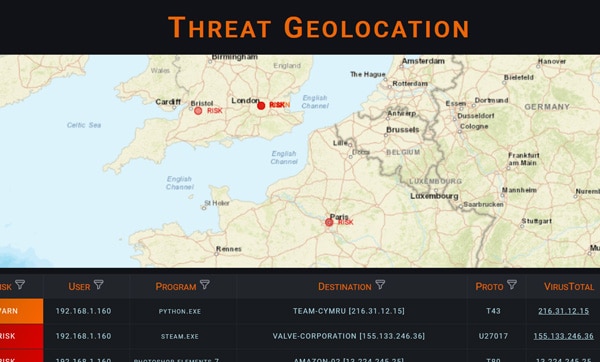
Explore all FOUR pages of the online Admin Portal:
Geolocate blocked threats:
- RISK – data blocked from unapproved applications.
- WARN – data blocked from being sent to a destination not associated with its parent application.
Check the legitimacy of the destination on VirusTotal.
NOTE: The sandbox takes a data feed from a real user. If the user is configured correctly, you may not see any breach alerts. You may need to change the display time period using the button on the top right.
Outbound data risk profile over time:
- APPS – data blocked from unapproved applications.
- DEST – data blocked from being sent to a destination not associated with its partent application.
NOTE: The sandbox takes a data feed from a real user. If the user is configured correctly, you may not see any breach alerts. You may need to change the display time period using the button on the top right.
Manage TRUSTED applications:
- An application not on this list has its data blocked from transmission.
- A trusted application can still have its data blocked from transmission if data is not sent to the defined trusted endpoint.
You will see examples of the granularity to which the application data integrity can be defined. Such as blocking any data requests for app updates not sent directly to the vendor.
NOTE: The sandbox is connected to a real user. We have disabled functionality that allows you to change the user’s configuration.
For example, you can see the user specific list of approved applications, but cannot change them.
User license management.
NOTE: The sandbox is connected to a real user. We have disabled functionality that allows you to change the user’s license setup.
Ready to try the real thing?
See first hand how ZORB blocks data theft, protecting your sensitive data and business reputation.
Let’s get you started today, with no risk
No credit card required
Want a one-to-one demo tailored to your business needs?
Book a live demo to learn how ZORB can eliminate data theft and protect your business.
Use Cases
Use Cases
Get inspired. Get protected.

Bad actors
Prevent data theft from hackers or disgruntled employees

Malware
Prevent data theft from C2C malware (botnets, RATs, ransomware)

Cloud applications data redirection
Prevent data threats to cloud application data during upload

Application risks
Prevent data threats from app misconfiguration or malicious updates
… more
Start your outbound security journey
TODAY
Add outbound data to your security posture.
Pricing
Affordable pricing for everyone
Ready to protect your sensitive data and business reputation?
1 - 50 licences
£69
per licence, per annum
1 - 500 licences
£65
per licence, per annum
1 - 1000 licences
£61
per licence, per annum
1000+ licences
£57
per licence, per annum
Billed annually. Excludes local taxes.
SOFTWARE LICENCE
+ TRANSMIT only trusted data
+ PREVENT compromised data becoming a breach
+ STOP hackers, insiders, botnets, ransomware
+ STOP cloud data redirection
+ STOP malicious application updates
+ STOP data bypassing the VPN
CLOUD DASHBOARD
+ GEOLOCATE blocked events
+ CORRELATE threat with VirusTotal
+ REALTIME outbound data risk posture
+ CUSTOMISABLE trusted application list
(Includes: 1 x admin licence per organisation)
EXTRAS
(Individually costed)
Additional ZORB cloud dashboard admin licence
Risk notifications to own helpdesk
Risk notifications to own SIEM
Upload network traffic to own SIEM
Or call the ZORB team on 01223 603029
10 FREE Licences, on us!
Start your outbound data protection journey TODAY.
See first hand how ZORB stops
– data theft from hackers, malware and insider attacks
– cloud data misdirection
– malicious updates
No credit card required
Blog
Our Blog
News, Insight, Prevention Tips: Protect your data security and data privacy.
Data Loss Prevention
Three Business Strategies Exposing Your Sensitive Data
2 November 2023
0 Comments14 Minutes
Cyber SecurityBreach Prevention
Keep Your Competitive Edge: Intellectual Property Makes you a Target
14 October 2023
0 Comments12 Minutes
Compliance
Get our best content in your inbox
All our tips, stories, breach advisories – straight in your inbox
Your privacy matters. You can unsubscribe at any time.
10 FREE Licences, on us!
Start your outbound data protection journey TODAY.
See first hand how ZORB stops
– data theft from hackers, malware and insider attacks
– cloud data misdirection
– malicious updates
No credit card required